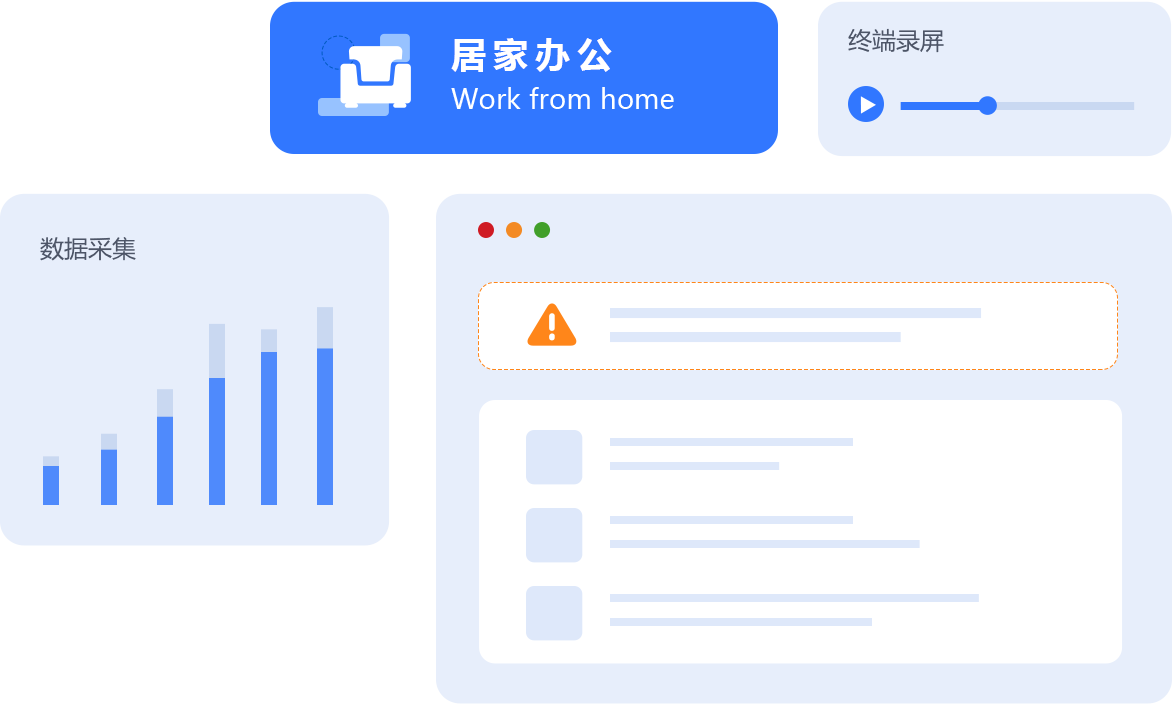
Terminal operation security
- Screen operation recording
- File operation record
- Document release monitoring
- Data tampering record
- Sensitive information monitoring
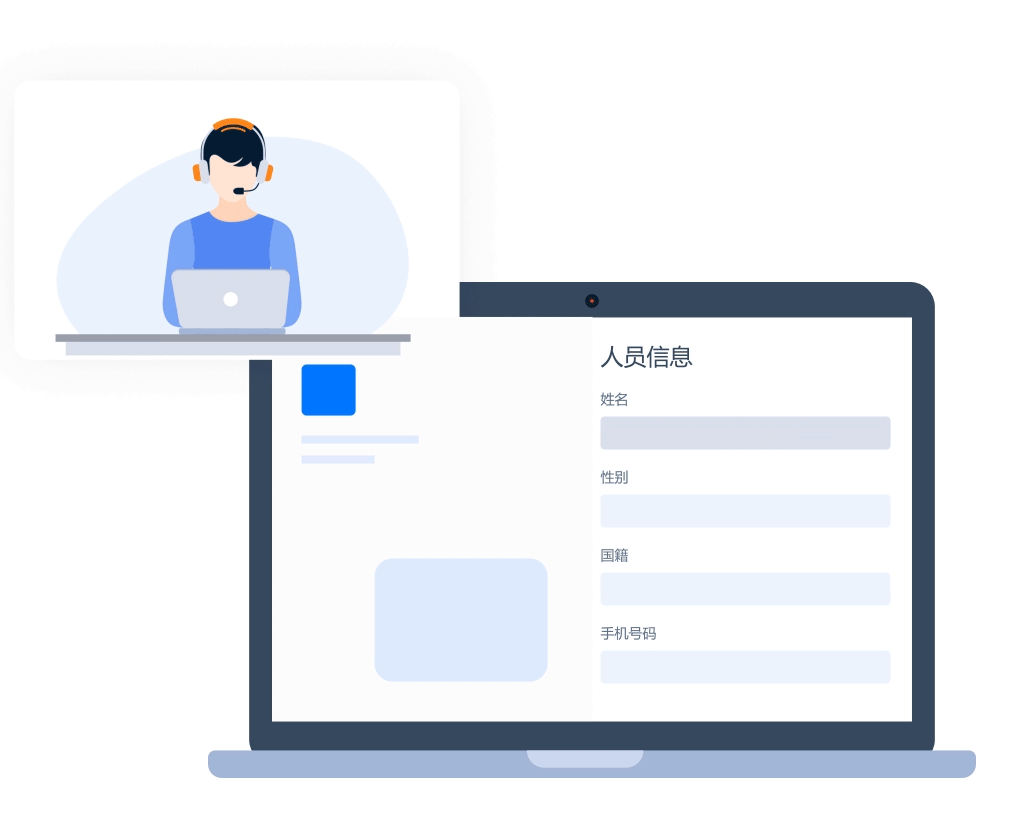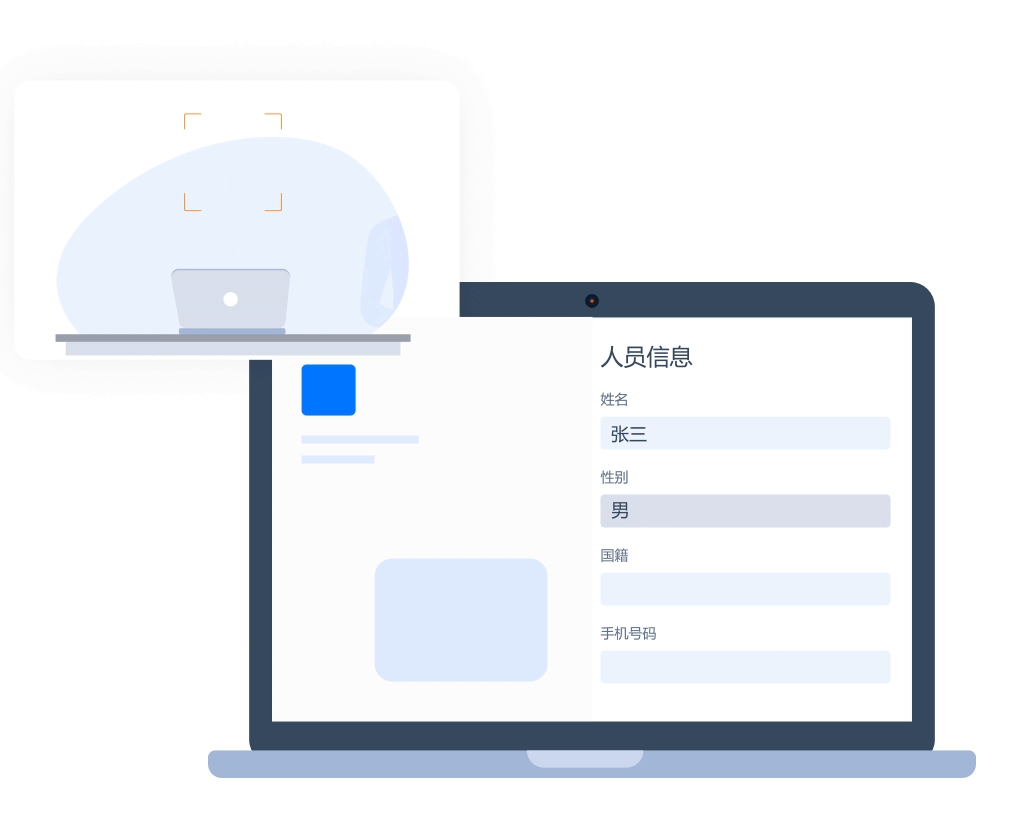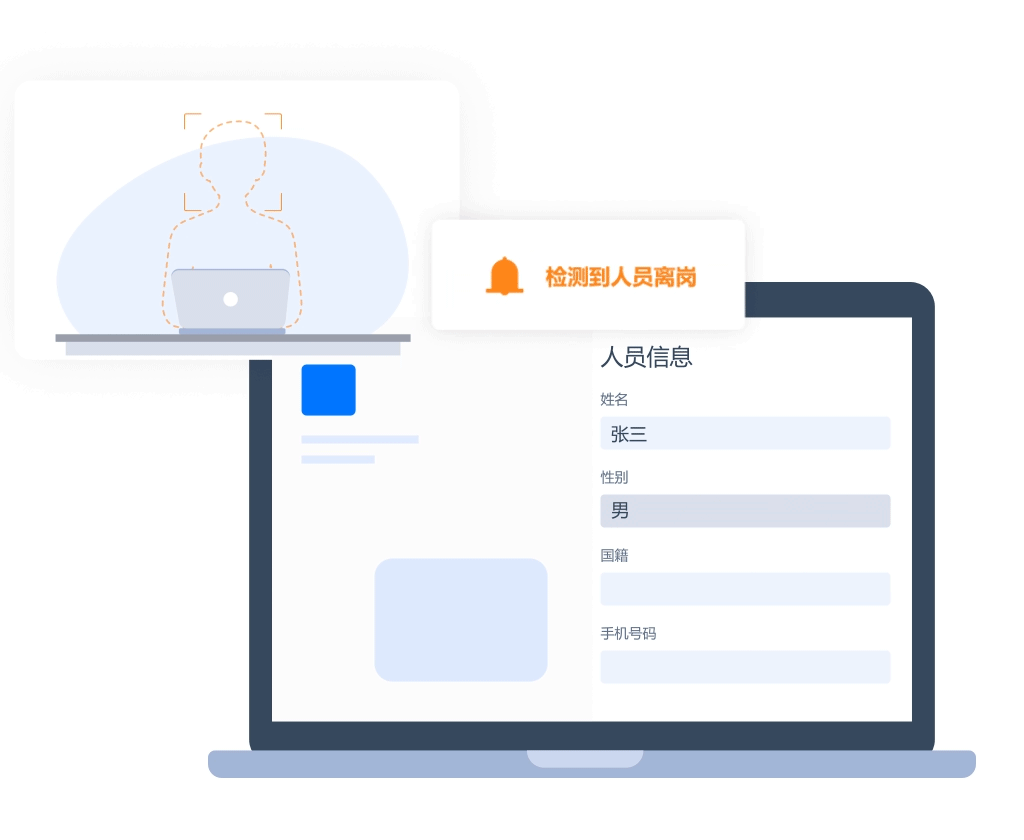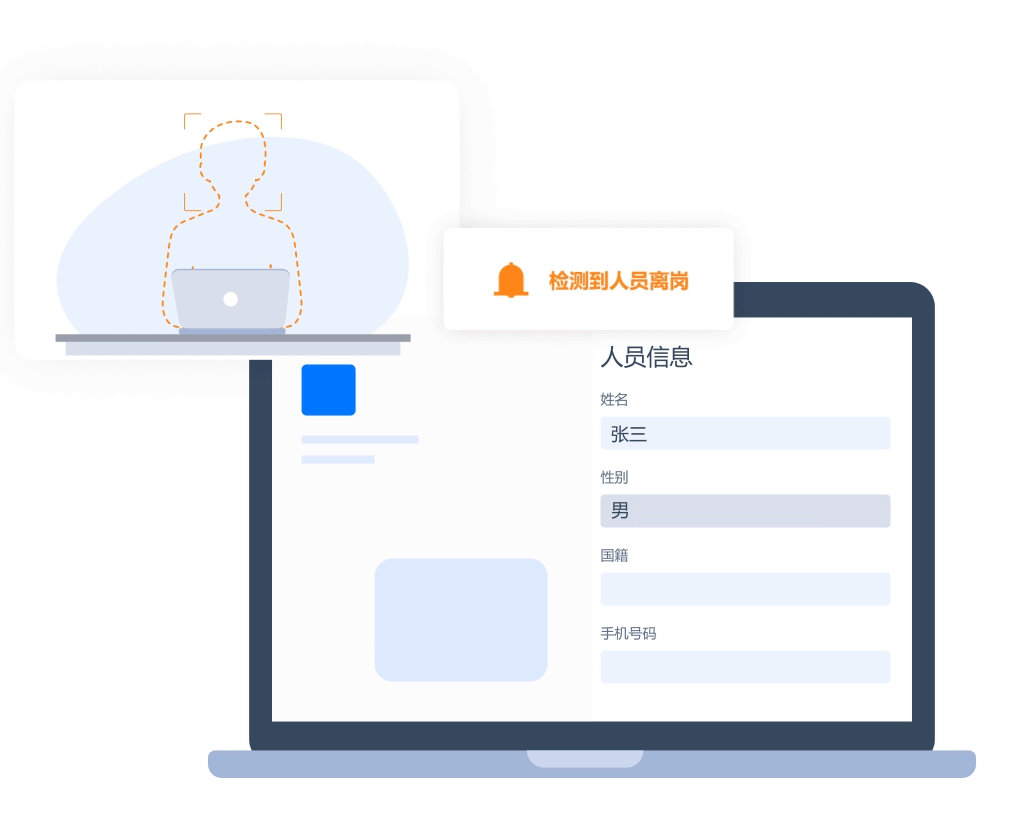
User behavior security
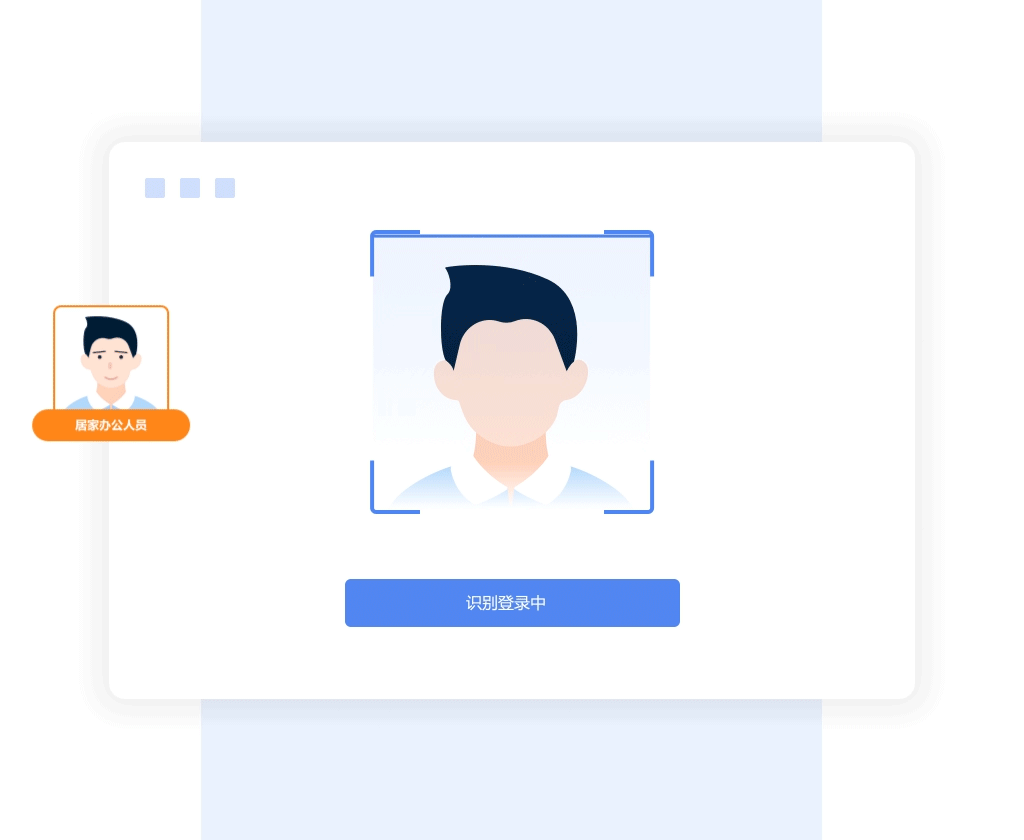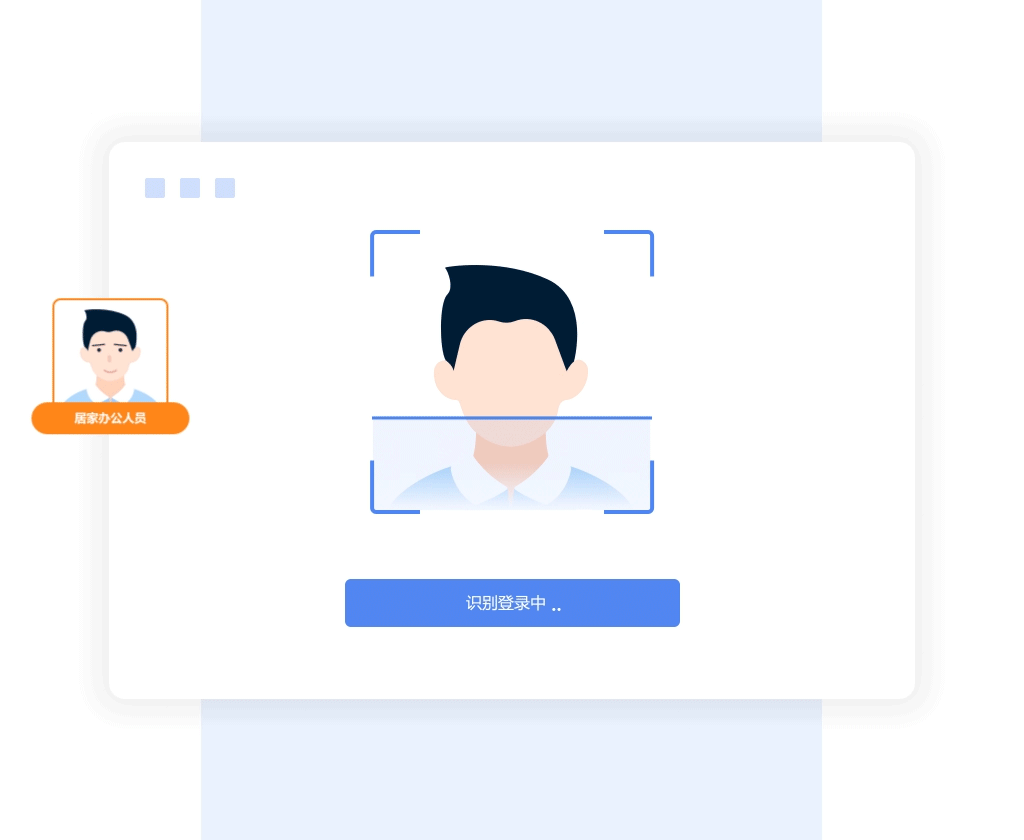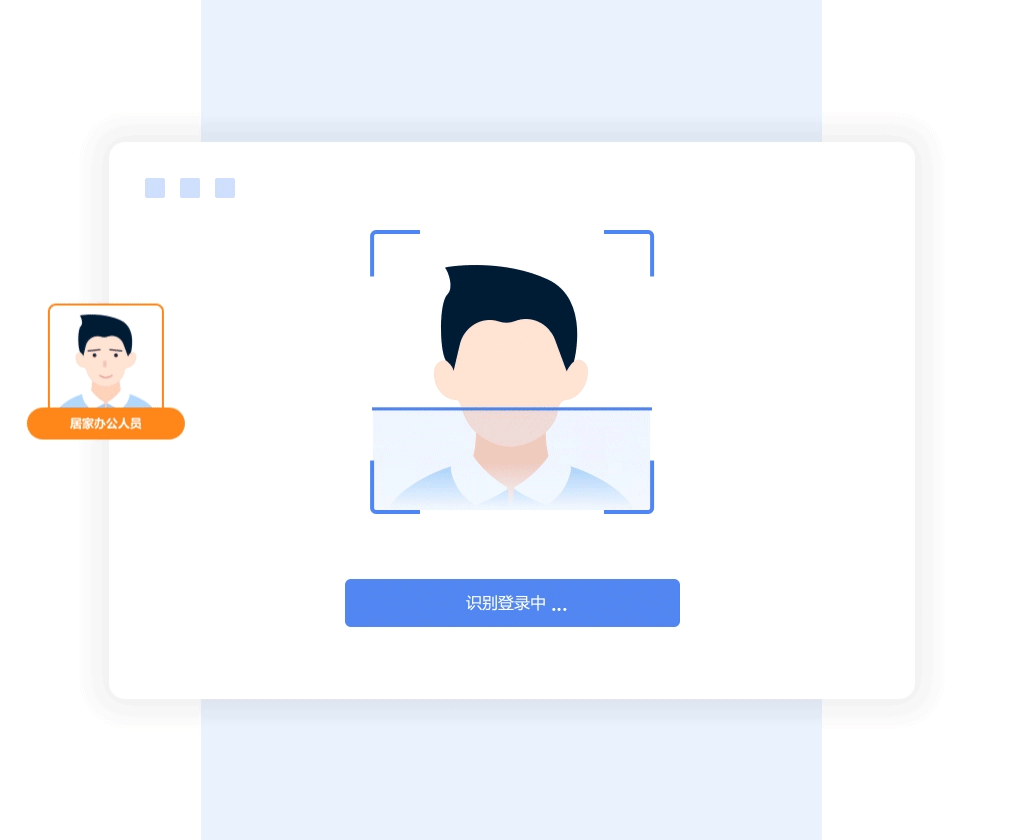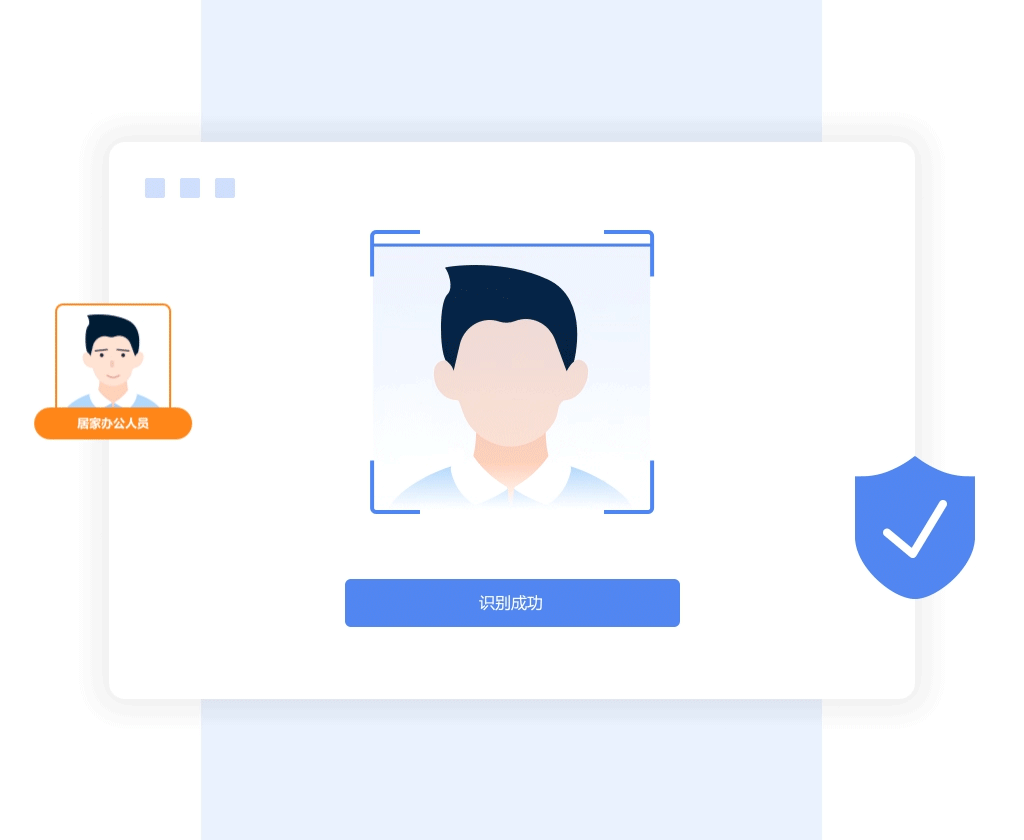
- Face authentication
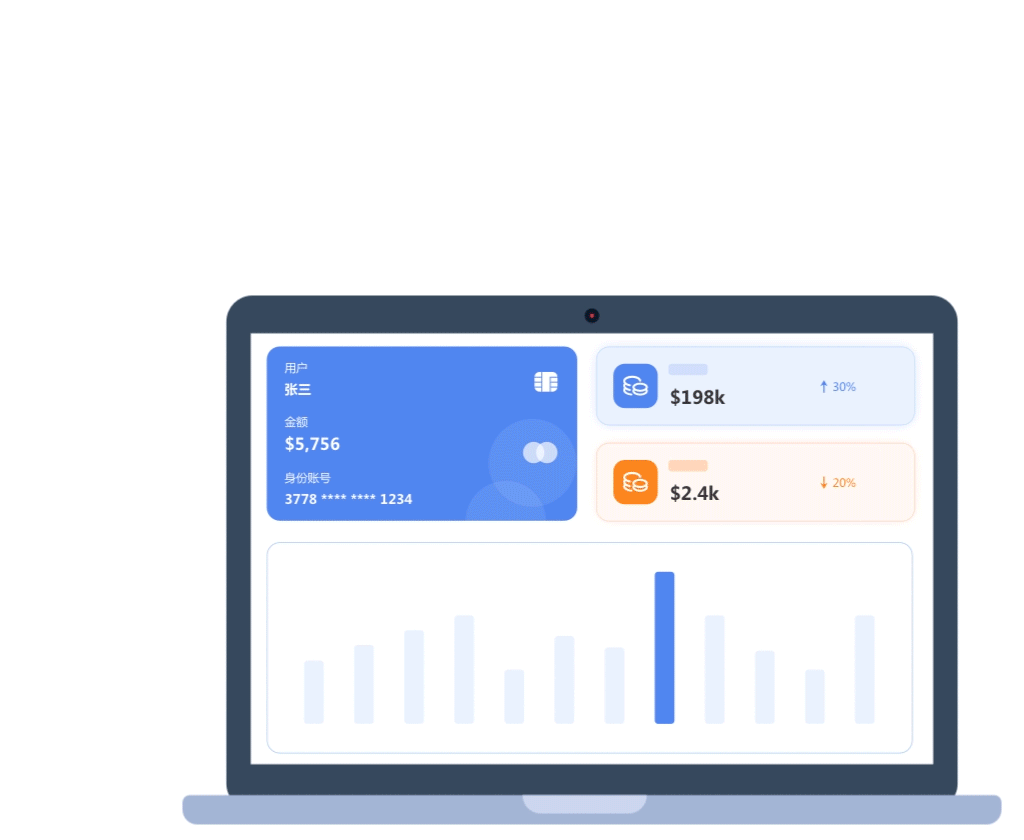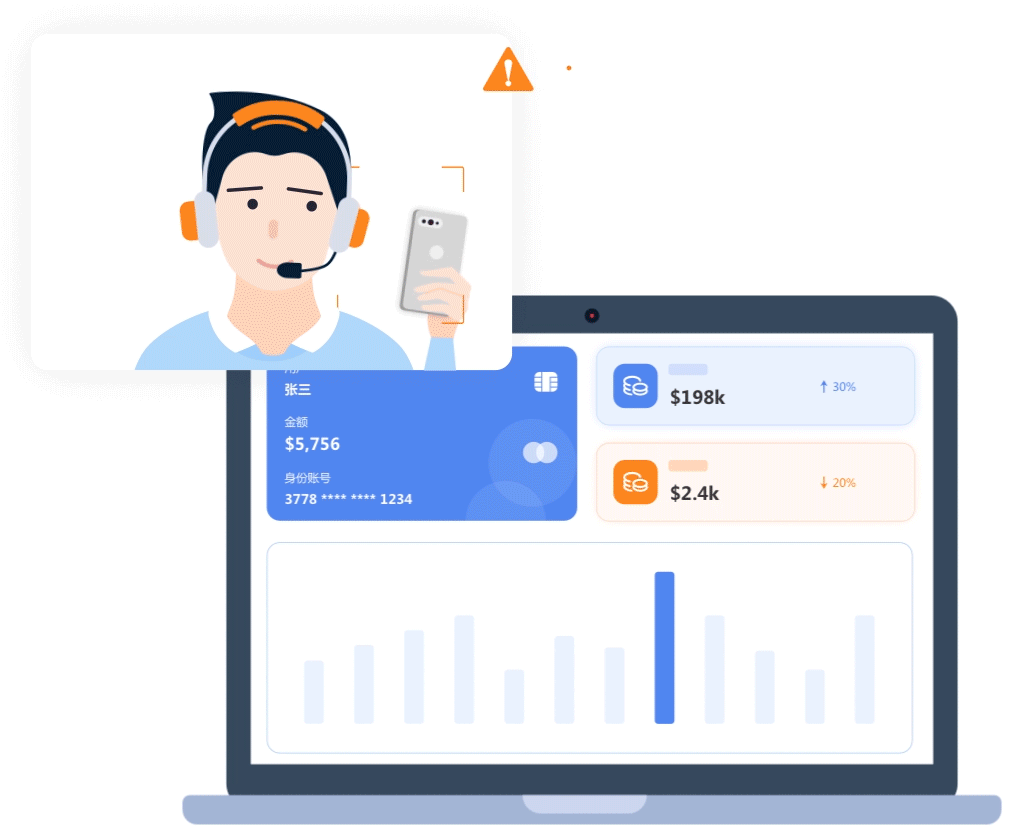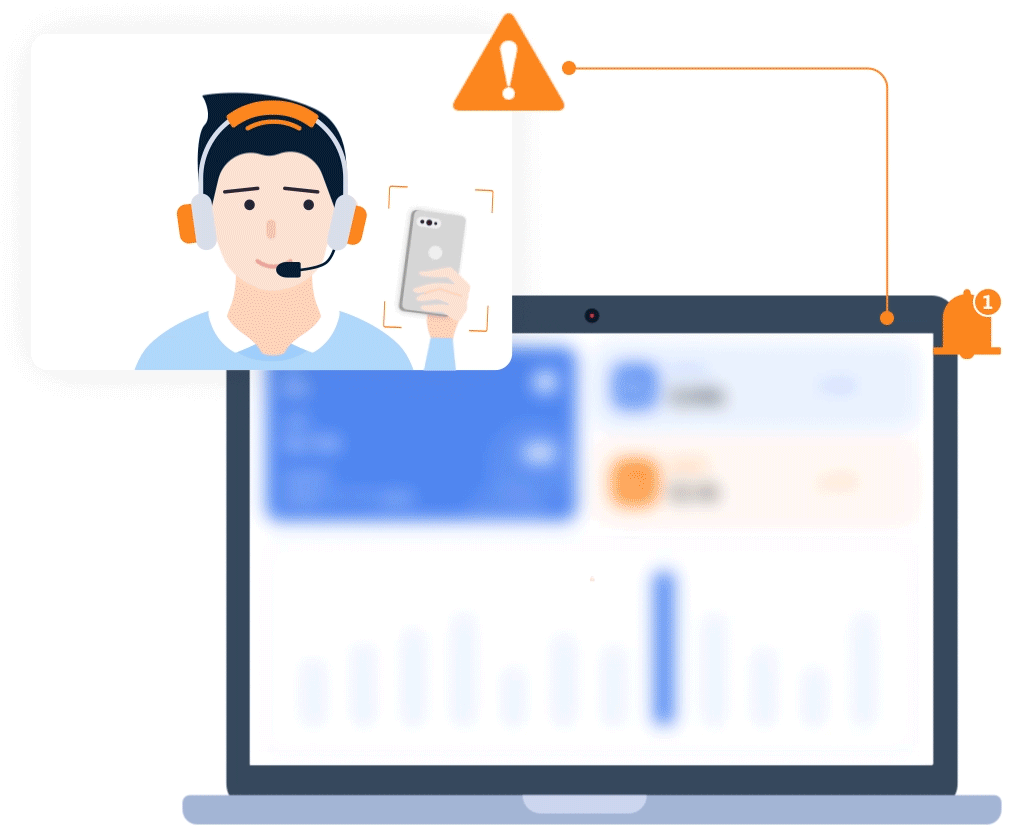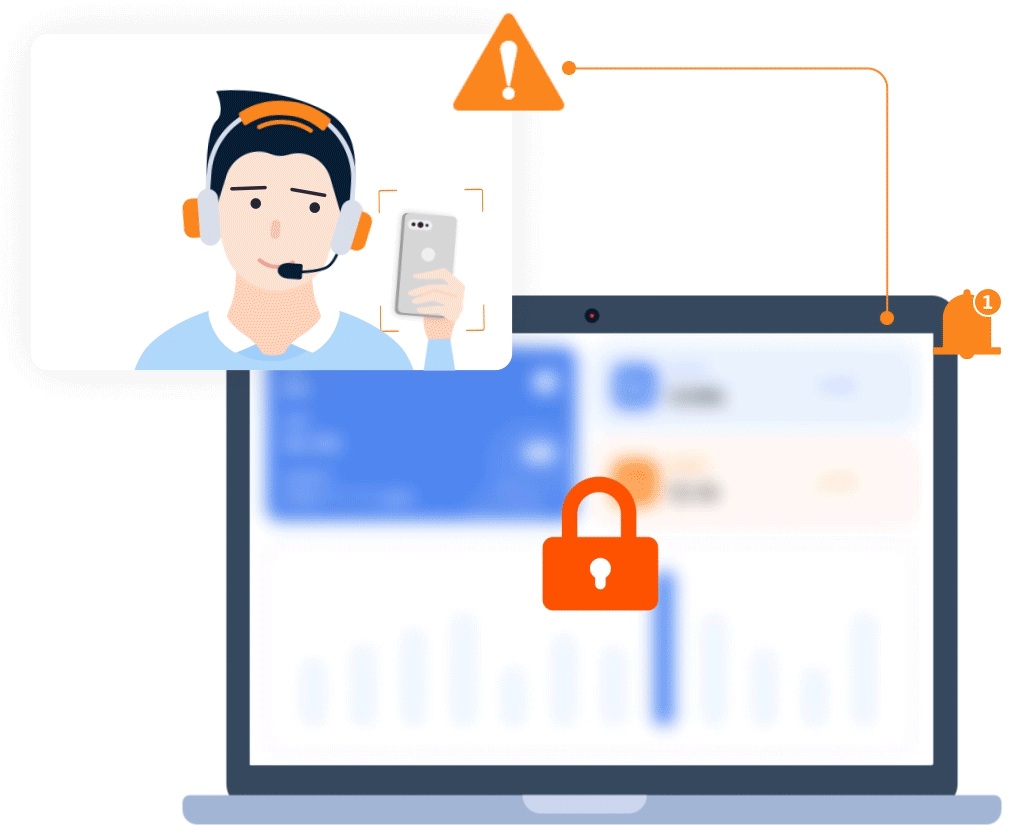
- Mobile phone photo recognition
- Identify two persons in the same frame
- Identification of writing on a desk
- Recognition of personnel leaving their posts

 Enterprise Platform
Enterprise Platform
 Discovery and Evaluation
Discovery and Evaluation
 Automation
Automation
 Industry Solutions
Industry Solutions
 General Solutions
General Solutions
 Partnership
Partnership
 Ecosystem Alliance
Ecosystem Alliance
 Consulting Services
Consulting Services
 Community
Community
 Company Introduction
Company Introduction
 News and Updates
News and Updates
 Contact Us
Contact Us