Recently, TSMC, the world's leading foundry company, revealed a major data leakage incident. Some employees illegally intercepted core technical information by means of mobile phone reproductions and other means while working at home. This incident not only exposed the management loopholes in the remote office scene, but also made enterprise information security become the focus of public opinion again. According to statistics, more than 60% of enterprises in the world have adopted the mixed office mode, but behind the convenience of remote collaboration, multiple crises such as equipment, operation and compliance are quietly lurking.
1.Safety dilemma of Home Office
Retrospection: whole process audit Retrospection
1.Safety dilemma of Home Office
Under the traditional office mode, enterprises can build a security defense line through physical isolation, access control system and monitoring equipment. However, in the remote office scenario, employees using personal devices to access the intranet, cross platform operation, and unattended terminals have become "high-risk windows" for data leakage.
In the TSMC incident, employees obtained confidential information by reproducing the screen on their mobile phones, which is precisely the use of the loophole of the lack of behavior monitoring in the remote environment. Under the mixed office mode, enterprises will face problems such as decentralized equipment management, untraceable operation behavior, and cross platform transmission of sensitive data. The traditional security system has become weak in the remote scenario.
2.I-Search solution builds a security system with behavior data
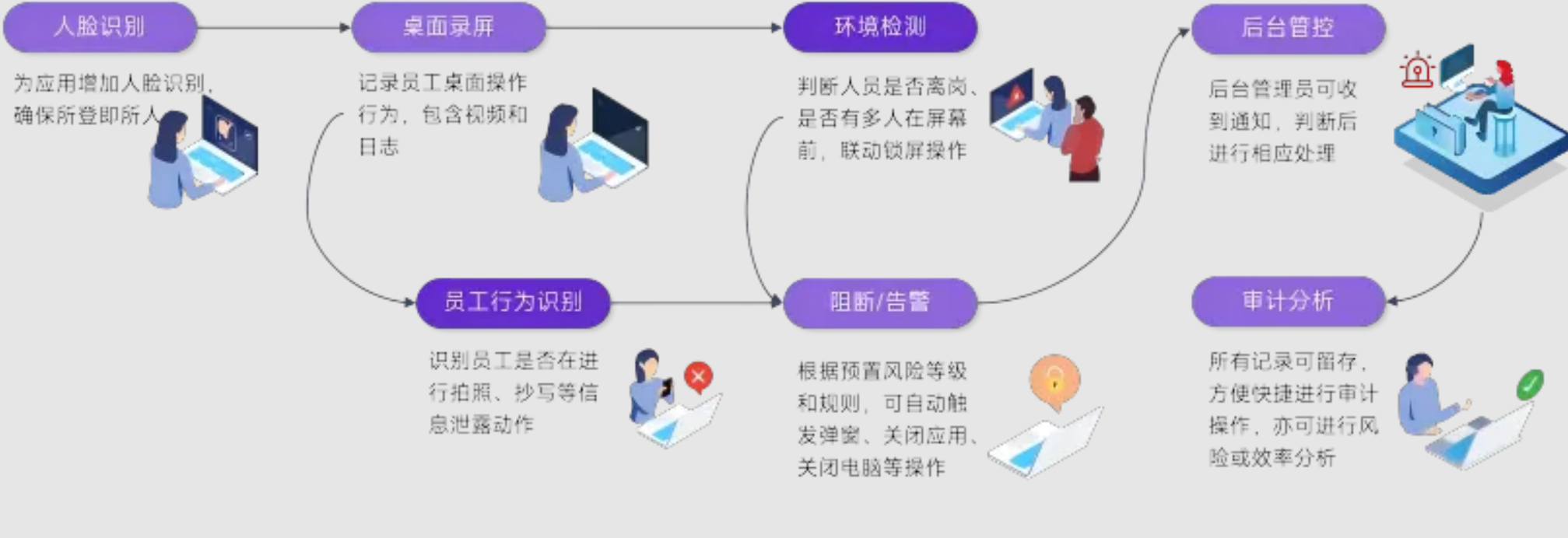
I-Search's home office solution adopts the "desktop+behavior" dual recognition mode. Through desktop screen recording and log recording, it realizes the real-time blocking alarm of equipment access and high-risk behavior.

Pre prevention: dual access control of equipment and behavior
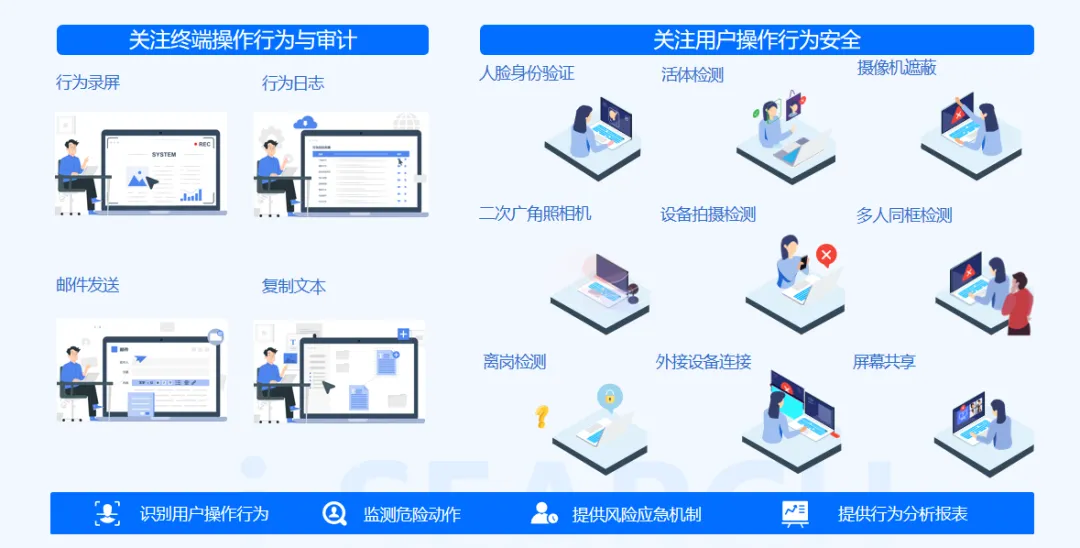
Device access control: collect information based on the keyboard, mouse and clipboard on the desktop, monitor whether there are actions such as copying and screenshots, and back up sensitive information such as customer information and technical parameters through external devices such as USB flash drives.
High risk behavior prediction, based on the big data analysis engine, the system automatically marks sensitive fields such as customer information and technical parameters, and immediately triggers an alarm and blocks the operation when employees try to capture, copy or transmit.
In process monitoring: whole process visualization and intelligent intervention
The whole process behavior monitoring uses the camera to record the human behavior of employees when operating sensitive applications/Web pages, and automatically identify high-risk operations such as mobile phone shooting, copying, multiple people in the same frame, and leaving the post.
Real time blocking alarm, real-time linkage, blocking the transmission of sensitive information by closing applications, closing terminals and other forms, and sending a letter to the back-end administrator to remind them of the risk of information disclosure, so as to effectively prevent the disclosure of sensitive information.
Retrospection: whole process audit Retrospection
Accurate data analysis, all data can be stored, and support text search, positioning, playback screen/video recording, so as to realize the rapid audit of sensitive behavior, and provide effective support for the cause insight, positioning and subsequent legal procedures of high-risk disclosure behavior.
The data storage is small. The above solutions do not need GPU support. All behavior recognition is completed on the client, and the resource occupation is no more than 5%, which does not affect the daily work of employees.

3.Not only guard security, but also enable business growth
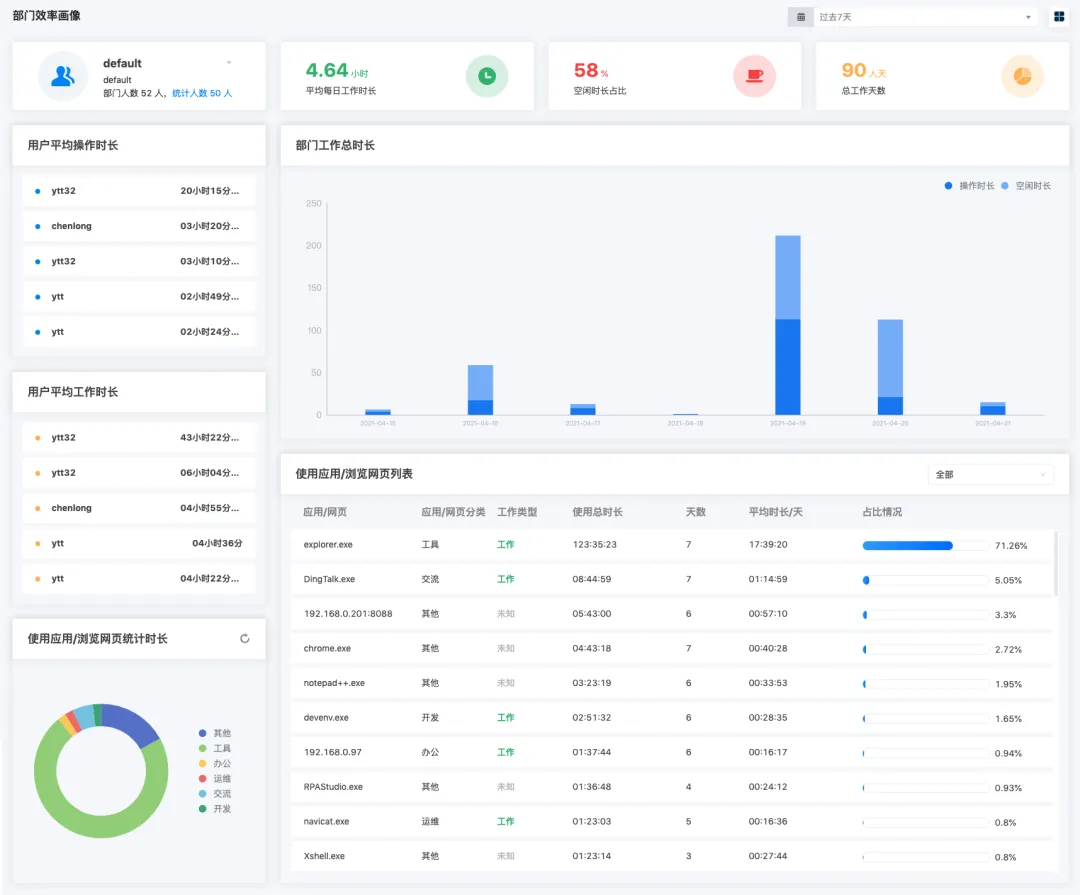
We are not only concerned about safety, but also committed to enabling business. Through the work efficiency portrait, employees' work efficiency can be evaluated from multiple dimensions. Provide objective basis for outsourcing settlement and performance appraisal scenarios, and provide efficiency optimization suggestions for managers.
- Support custom application/Web page types, such as entertainment, office, communication, etc
- Support statistics of usage type proportion and detailed usage analysis
- Integrate the collected behavior log data into a visual report to show the comparison of work efficiency between departments or between different employees

TSMC's disclosure is not an isolated case. With the increasingly complex office environment and diversified means of disclosure, information security of high-tech enterprises is facing multiple challenges.
I-Search relies on 15 years' experience in the field of super automation to solve the security dilemma of remote office with technological innovation and help enterprises achieve a win-win situation of safety and efficiency in the era of mixed office.

 企业平台
企业平台 发现评估
发现评估 自动化
自动化 行业解决方案
行业解决方案 业务解决方案
业务解决方案 合作伙伴
合作伙伴 生态联盟
生态联盟 咨询服务
咨询服务 培训服务
培训服务 交流社区
交流社区 客户成功
客户成功 产品文档
产品文档
 公司介绍
公司介绍 新闻列表
新闻列表 联系我们
联系我们 加入我们
加入我们

