What can CDA provide?
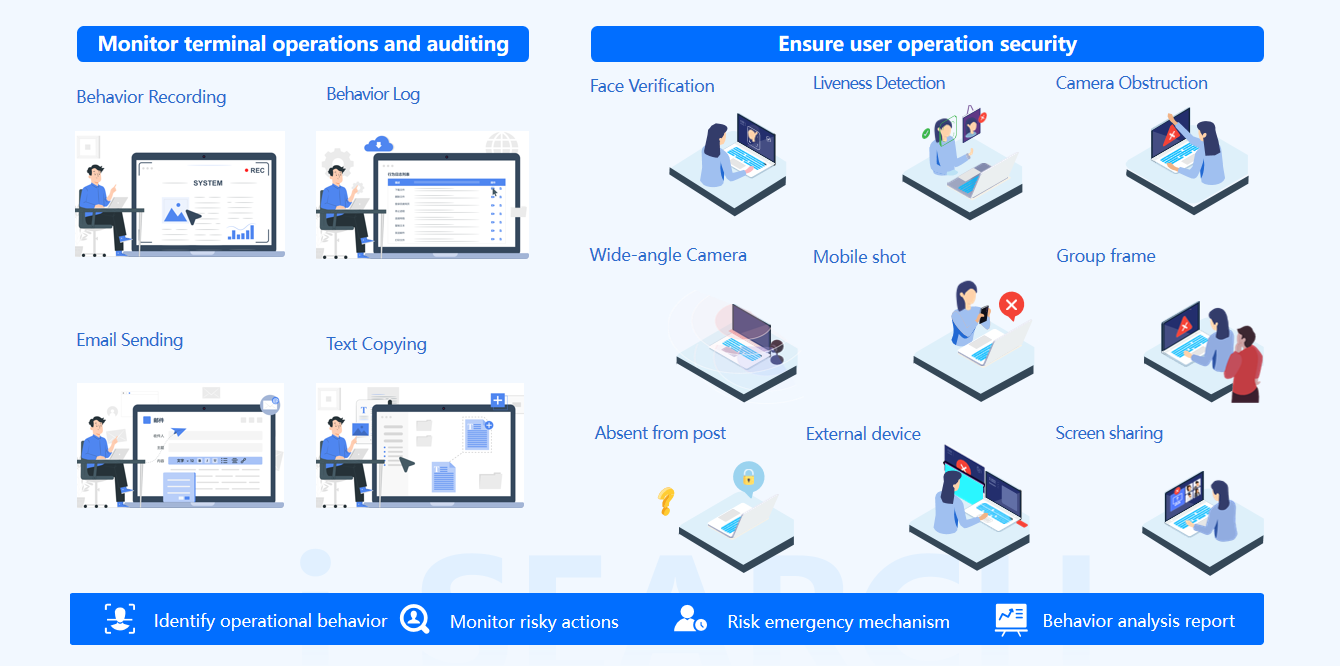
1. iS-CDA-Agent: Utilize liveness detection facial biometric technology for identity verification of remote office staff.2. iS-CDA-Control: Used to receive and manage violations transmitted by the Agent, issue warnings and block violations. It can also distribute warning policies to the Agent through Control, and supports the analysis and statistical display of risky behaviors and users.
3. Sensitive information protection capability, based on desktop keyboard, mouse, clipboard for information collection, monitoring whether to copy customer sensitive information and copy user sensitive information through USB drive.
4. Automated monitoring capability, which allows remote management of monitoring agents through the platform, change Agent status, intervene timely in case of dangerous operations, and also monitor the application and specific usage of the agents.
5. iS-CDA-Yolo Model detection: Based on the Yolo model, it can identify high-risk actions such as taking photos with a mobile phone, transcribing, multiple people in the same frame, and absence from the post among home office staff, empowering safe home office operations for companies.
CDA Feature List
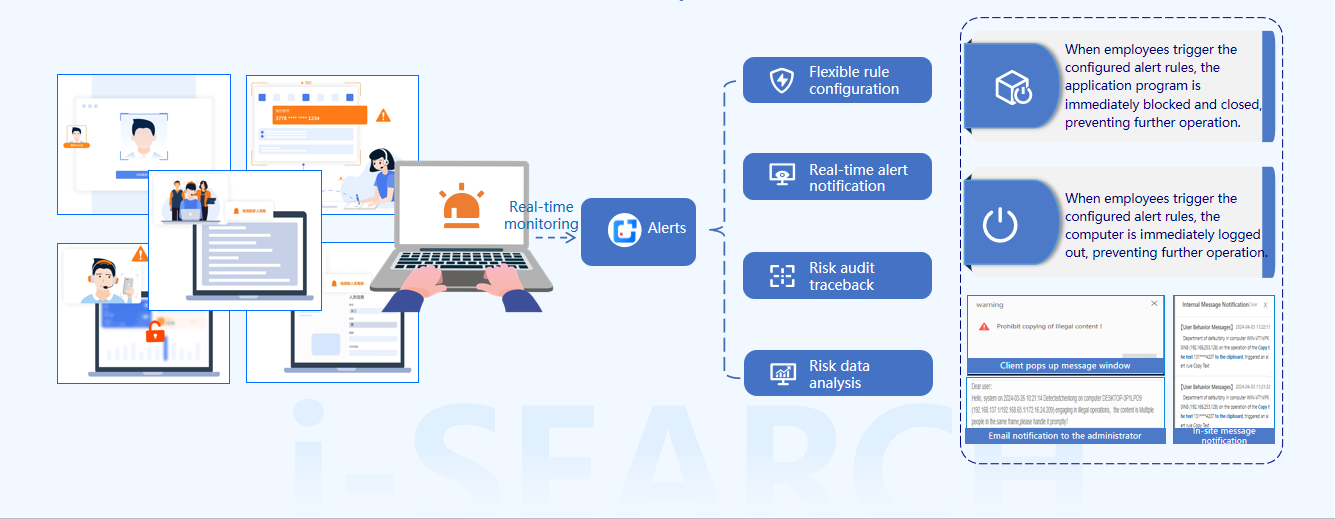
Supports various risk control methods, timely risk blocking
Enhances risk control capabilities, effectively reduces risky behaviors, timely intervenes in risky operations, and avoids unnecessary losses.

 企业平台
企业平台 发现评估
发现评估 自动化
自动化 行业解决方案
行业解决方案 业务解决方案
业务解决方案 合作伙伴
合作伙伴 生态联盟
生态联盟 咨询服务
咨询服务 培训服务
培训服务 交流社区
交流社区 客户成功
客户成功 产品文档
产品文档
 公司介绍
公司介绍 新闻列表
新闻列表 联系我们
联系我们 加入我们
加入我们

